Galem KAYO
on 17 November 2020
Cybersecurity attacks on industrial IoT solutions can have detrimental consequences. This is the case because IoT devices record privacy-sensitive data and control production assets. Therefore, demonstrable trustworthiness is prerequisite to IoT adoption in industrial settings.
Fortunately, IT security is a mature field. Experts have identified classes of threats devices may be subject to. Let’s discuss these threat patterns and mitigation strategies in the IIoT context.
Threat modelling: what can go wrong?
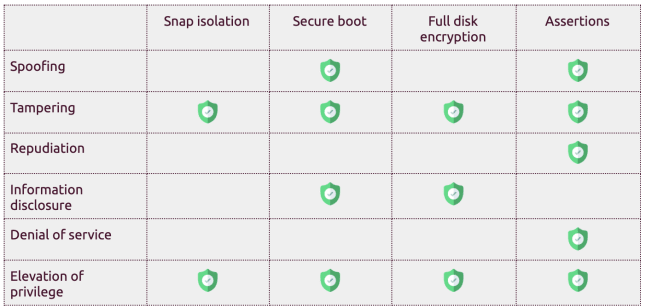
Cybersecurity practitioners often use threat models to map attacks that might compromise a system. The STRIDE model developed by Microsoft is widely used for threat modelling. Here are examples of threats for IoT devices.

Following are key operating system features that mitigate these threats.
Authenticating software with secure boot
IoT devices are most vulnerable at boot. Initiating the OS with malicious software components could lead to the total corruption of a device. This type of breach exposes devices to additional security threats.

Secure boot verifies that software is authentic and originates from a trustworthy source. This verification prevents boot process alteration. A component therefore executes, only if its digital signature is validated by the preceding component.
The firmware validates the bootloader using a public key stored on-device (root of trust). The bootloader then validates the kernel, which in turn deciphers the root file system. The result is a software chain of trust.
Protecting data with full disk encryption
IoT devices store data from sensors installed in privacy-sensitive environments. Threat actors can extract confidential information, trade secrets or intellectual property, if they gain access to such data. information disclosure can lead to other vulnerabilities.
How then to protect data stored on the disk from unauthorised access? The answer is encryption of the whole disk or of key partitions. For this purpose, the operating system uses a single key to encrypt and unencrypt data. This key is stored on a separate disk partition.

Wouldn’t it then suffice to know the storage location of that key to unlock the disk? The answer is no, because that key is itself encrypted. It thus has to be unencrypted with a master key. The master key is usually stored on the chip, or on special-purpose external devices (like TPMs or secure elements).
Locking down devices with digital signatures
Constraining the behavior of IoT devices reduces the surface of attack. Locking down actions susceptible to lead to any STRIDE mode of attack during uptime is an effective defense strategy. Highly secure operating systems can orchestrate digital signatures to lock down such actions.

Behaviors that the OS can control using digital signatures are: authentication, communication and app execution. Authenticating devices controls access privileges. Restricting addresses a device can accept traffic from creates a barrier to spoofing and DoS attacks. Locking down the software bill of materials allowed on a device prevents tampering with apps.
A resilient endpoint security mix
Strong endpoint security is essential in a defense in depth strategy for IIoT . However, most Linux distributions do not provide security capabilities like secure boot, full disk encryption or digitally signed assertions out of the box. This results in additional costs for developers to build trustworthy IIoT devices.
Ubuntu Core offers advanced security capabilities by default. The operating system orchestrates the features described above to mitigate cybersecurity threats. This empowers any innovator to create IIoT appliances suitable for use in mission-critical environments like factories, smart cities and more.



